| Censorship | Umbrella |
| Introduction | Amplified Attacks |
| Brute Force | Futures |
| Selective Cutoff | Books |
| Commercial Software | Links |
Censorship
The attempt to silence a man is the greatest honour you can bestow on him. It means that you recognise his superiority to yourself.
~ Joseph Sobran (1946-02-23 age:72)
If you have a controversial site, sooner or later someone will try to take you down. The simplest way to do this is called a DOS (Denial of Service attack) . They use computers to bombard your site with page requests, hoping to overwhelm your server and slow response time so much that your users give up. Sometimes they uses viruses to commandeer armies of computers to co-operate in the attack from all over the world.
DDoS (Distributed Denial of Service Attack) .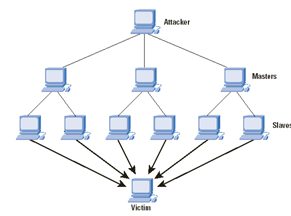 |
| simple distributed DoS attack |
What can you do to protect yourself?
The way I handle it is with brute force. My servers and pipes are so large and powerful most DOS attacks have no effect. You might consider moving your website to Google hosting or someone with overwhelming capacity. Your attackers will give up if they see they are having no effect.
What you have to do is track who a request is coming from and if they start hammering you, cut them off for an hour or so. But you have to allow search engine spiders in. If your attackers are not too bright, the will try to overwhelm you will just one computer. Unless you are on a home server, you probably will not even notice.
DOS attacks are a type of warfare with the attackers constantly evolving new methods of attack. There are dozen of techniques they use besides simply pretending to be an army of users. You may need to install commercial software on your server to deal with the problem if your attackers are sophisticated.
If you host your website on a cloud run by a big company like Google, Amazon or CloudFlare, any DDoS is likely just going to bounce off or be dealt with by their security people.
There are ways of amplifying a DOS attack. For example, an NNTP (Network News Transfer Protocol) server can be tricked into sending a long list of users where requested the time to a victim. In theory, there are ways to shut down the entire Internet with attacks streaming terabits of data at hapless servers. We really need to stop and resdesign the Internet with malware and security in mind. One feature it would have is a way to ask the Internet to block unwanted traffic at the source, ensuring, of course, such requests could not be counterfeited.
DOS attacksTo help deal efficiently with DOS attacks, we need a way in Internet protocol to block users from sending anything to a given IP as close to the source as possible for some time period. That way the site under attack does not have any extra overhead once an attacker is identified and the attackers do not swamp the Internet backbones with their attacks.
 |
recommend book⇒DDoS 90 Success Secrets: 90 Most Asked Questions On DDoS - What You Need To Know | |||||||||||||||||||||||||||||||||||||||||||||||||||||||
| by | Jack Huff | 978-1-4885-2536-0 | paperback | |||||||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| publisher | Emereo Publishing | 978-1-4885-3361-7 | eBook | |||||||||||||||||||||||||||||||||||||||||||||||||||||
| published | 2014-07-06 | B00QE3W2NU | kindle | |||||||||||||||||||||||||||||||||||||||||||||||||||||
| This is about strategies to protect yourself from distributed denial of service attacks. They are among the most privitive forms of attack and one of the hardest to fight on your own. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Greyed out stores probably do not have the item in stock. Try looking for it with a bookfinder. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||
This page is posted |
http://mindprod.com/jgloss/dosattack.html | |
Optional Replicator mirror
|
J:\mindprod\jgloss\dosattack.html | |
 |
Please read the feedback from other visitors,
or send your own feedback about the site. Contact Roedy. Please feel free to link to this page without explicit permission. | |
| Canadian
Mind
Products
IP:[65.110.21.43] Your face IP:[18.117.168.139] |
| |
| Feedback |
You are visitor number Statcounter | |